Some background: I run a small software consulting firm, but I’m also a family doc and I keep a few thousand pages of clinical notes in a semantic mediawiki (“NotesWiki”) that I host on my own servers. I wanted network redundancy of this NotesWiki so I enlisted my parent’s network 150 miles away. On my parents network I installed a proxmox VM server and placed the VM server on a separate subnet from my parents local subnet. There are lots of ways to do this using debian/Proxmox, but I decided to use a ddwrt router as the subnet separation point (me7). See drawing below for an explanation of my network.
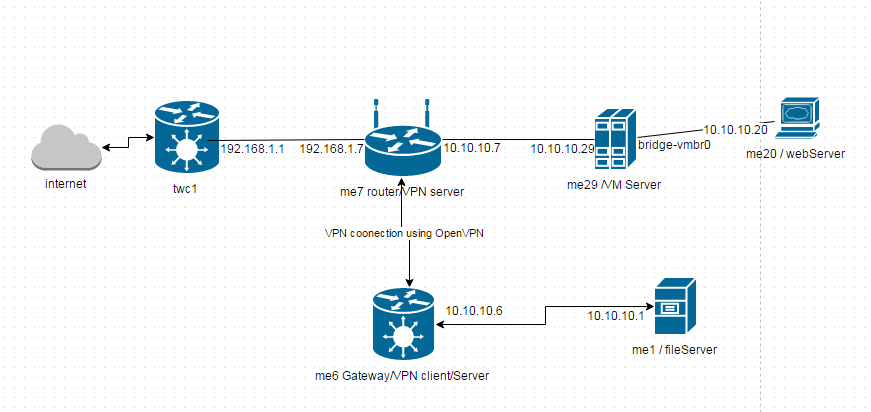
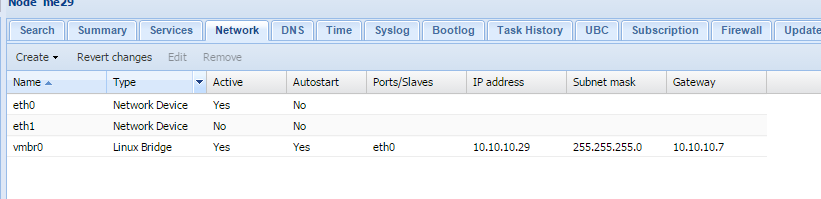
This setup seemed easy enough but for some reason I could not direct network traffic from the internet to me20 (the webserver) despite correct port forwarding in twc1. After days of pinging, packet watching w/ wireshark, and pulling my hair out, I finally figured out what was going on. me20 is a virtual machine that sits on a proxmox VM Server (me29). I had set me29’s gateway as 10.10.10.6 (me6) and this meant that packets which arrived at me20 from the internet would take a return path through me6. Obviously this didn’t work. The solution was to set the gateway to the a more appropriate outgoing route (e.g. 10.10.10.7). See proxmox config image below.
I hope this post saves someone else the frustration I experienced.